Abstract.
The purpose of this document is to provide guidance on how to configure both of the tools mitmproxy and ettercap to work together to monitor mobile application traffic. This document is intended for educational purposes. Using the techniques here with malicious intent may result in criminal consequences. Before going any further, I want to point out one of the better quotes that I have seen in a man file :-). Below can be found in the man file of ettercap."Programming today is a race between software engineers striving to build bigger and better idiot-proof programs, and the Universe trying to produce bigger and better idiots. So far, the Universe is winning." - Rich Cook
Install ettercap
Homebrew is amazing. Ettercap is as easy to install as issuing the following command.brew install ettercap
Install mitmproxy
The docs for mitmproxy are fairly straightforward. Mitmproxy is a python package that runs on Python 2.7. The link below has the official documentation. http://docs.mitmproxy.org/en/latest/install.html#installation-on-mac-os-xConfigure Port Forwarding
First enable IP forwarding. This is outlined in the transparent proxy guide in the following link,. http://docs.mitmproxy.org/en/latest/transparent/osx.html.sudo sysctl -w net.inet.ip.forwarding=1
Brian John does an excellent job explaining the new port configuration that needs to occur for OS X Mountain Lion. See the link below for his guide. http://blog.brianjohn.com/forwarding-ports-in-os-x-el-capitan.html I will go through the steps necessary for mitmproxy to work as expected based on the information that Brian John provided.Create the anchor file.
/etc/pf.anchors/mitm.pf
Add the following lines to the anchor file, mitm.pf.
rdr pass on en0 inet proto tcp from any to any port 80 -> 127.0.0.1 port 8080
rdr pass on en0 inet proto tcp from any to any port 443 -> 127.0.0.1 port 8080
Create the pfctl config file.
/etc/pf-mitm.conf
Add the following lines to the pfctl config file.
rdr-anchor "forwarding" load anchor "forwarding" from "/etc/pf.anchors/mitm.pf"
Enable or Disable Port Forwarding.
To activate or deactivate port forwarding, use one of the following commands.Enable.
sudo pfctl -ef /etc/pf-mitm.conf
Disable.
sudo pfctl -df /etc/pf-mitm.conf
Combining the tools.
Now that port forwarding is now configured, fire up mitmproxy with the following command.python2.7 mitmproxy -T --host
mitmproxy will by default listen for incoming HTTP and HTTPS traffic on the proxy port 8080. Next, use the following command to start ARP spoofing the target device.sudo ettercap -T -M arp:remote /
The final command should look something like the following.
sudo ettercap -T -M arp:remote /192.168.0.1//80,443/ /192.168.1.54///
You will need to trust the mitmproxy CA if you would like to inspect HTTPS traffic. The steps for this configuration can be found in the following link, http://docs.mitmproxy.org/en/latest/certinstall.html. Once mitmproxy and ettercap are both running, then you should be start seeing network traffic from your mobile device on your OS X device. Good Luck with inspecting traffic! Let us know in the comments below if you have any questions or feedback on this article. Brooks
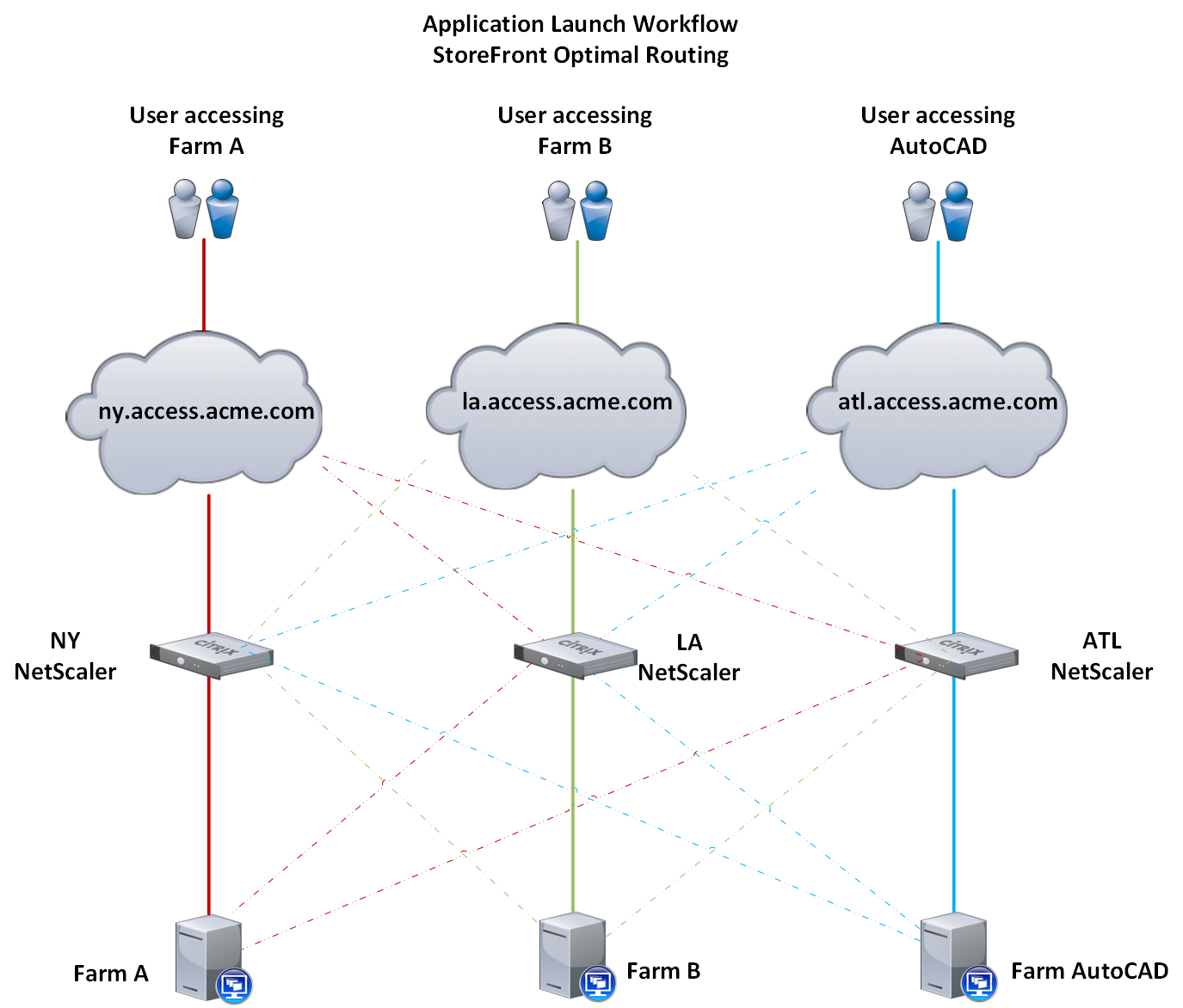
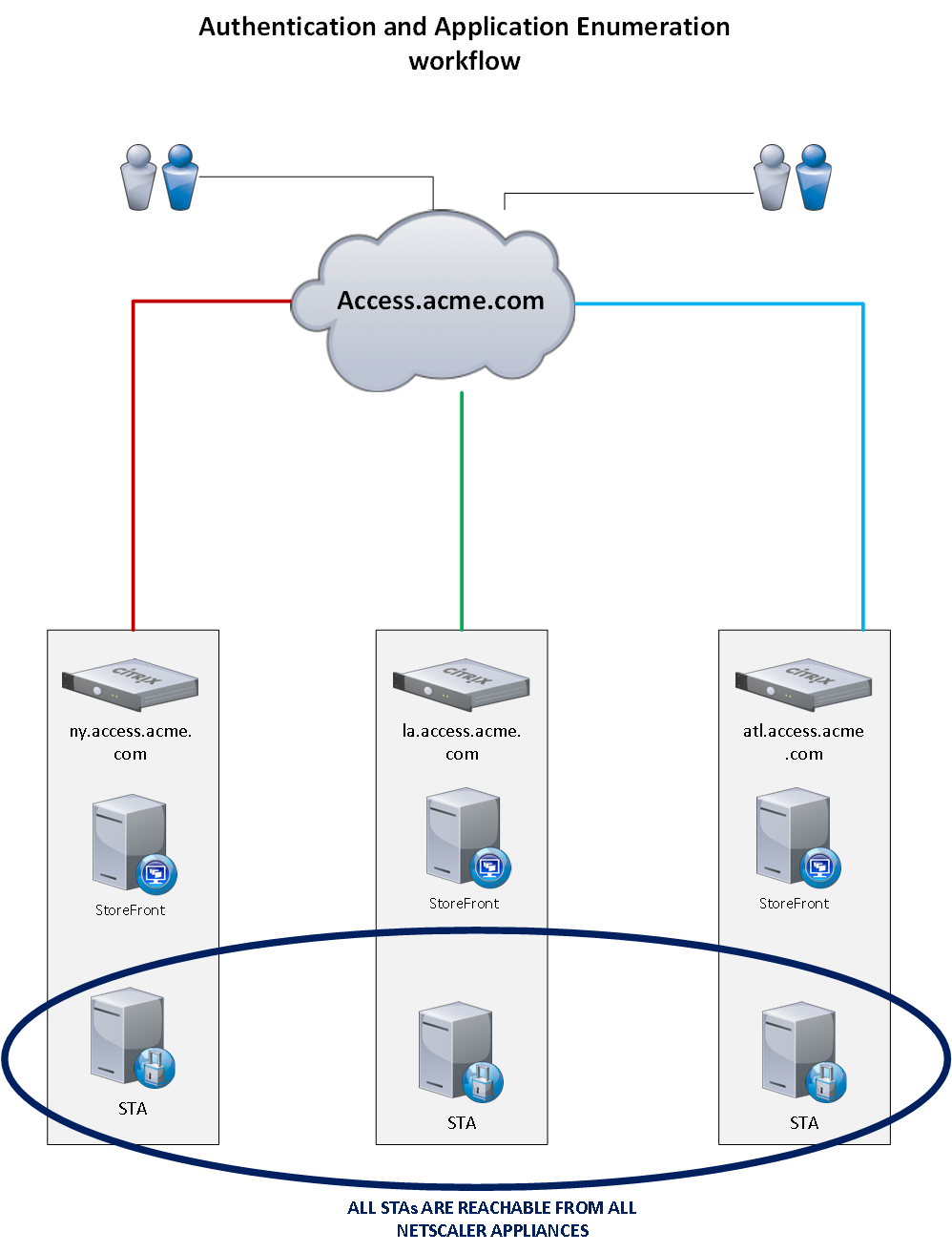 The diagram below illustrates the application launch workflow. The thick lines represent normal working conditions. The dotted lines represent the backup workflow in the event that site is experiencing an outage.
The diagram below illustrates the application launch workflow. The thick lines represent normal working conditions. The dotted lines represent the backup workflow in the event that site is experiencing an outage.
 Thank you for reading. I hope you found this beneficial. Please let me know if you have questions in the comments below.
BC
Thank you for reading. I hope you found this beneficial. Please let me know if you have questions in the comments below.
BC
 If no issues are found at the queried XML Broker, then the script will wait 5 seconds and move to the next XML Broker in the list. If you need to manually stop the script, then use CTRL+C or just close the window where the application is being executed. When an error is found, then I can logon on to the Director server and begin troubleshooting.
If no issues are found at the queried XML Broker, then the script will wait 5 seconds and move to the next XML Broker in the list. If you need to manually stop the script, then use CTRL+C or just close the window where the application is being executed. When an error is found, then I can logon on to the Director server and begin troubleshooting.
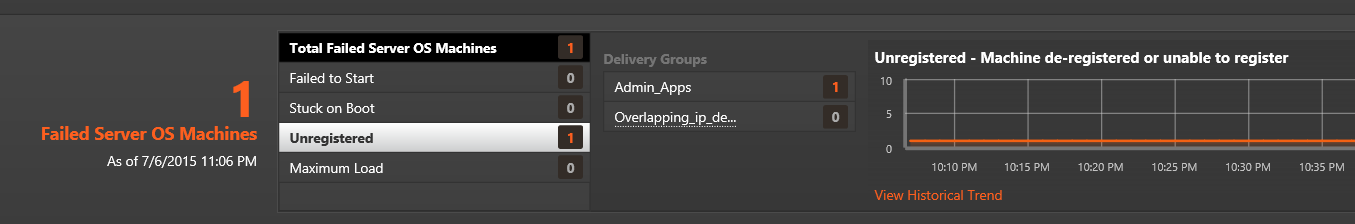 Each query is targeted at the URL “/Citrix/Monitor/OData/v2/Data/FailureLogSummaries”. The first
Each query is targeted at the URL “/Citrix/Monitor/OData/v2/Data/FailureLogSummaries”. The first